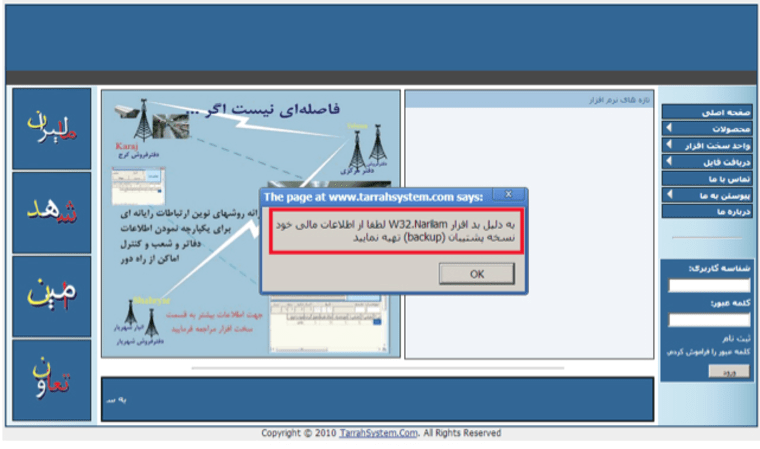
A new worm that appears to be targeted at Iran seeks to sabotage corporate databases by searching for specific phrases and values and replacing them with random ones.
This latest bug, dubbed the "Narilam" worm, goes after Microsoft SQL databases, according to Symantec, which first uncovered the malicious code.
Despite its ability to destroy databases, it may be cold comfort to its victims to know that Narilam does not steal data.
"The malware does not have the functionality to steal information from the infected system," Shuinchi Imano, a Symantec security researcher, said. "[It] appears to be programmed specifically to damage the data within the targeted database."
Imano went on to say that the "vast majority" of affected Symantec customers were corporate users and not individual consumers. The worm searches for words related to financial accounts in English and Persian.
Hackers, some of them state-sponsored, have targeted corporate and government servers in Iran in the past. The infamous Stuxnet worm, a collaboration between the United States and Israel, temporarily crippled Iran's nuclear development program in 2010. Earlier this year, the extremely sophisticated Flame spyware was found infecting computers in Iran's oil ministry.
Narilam is unusual because of its ability to write updates to a SQL database, Imano said, and businesses without backups will have great difficulty recovering from the attack.
"The affected organization will likely suffer significant disruption and even financial loss while restoring the database," he added. "Those affected by this threat will have a long road to recovery ahead of them."
However, it's not clear whether Narilam is playing in the same league as the state-sponsored bugs. Kaspersky Lab, which has found several likely cyberweapons in the past couple of years, doesn't think this one qualifies.
"Narilam is a rather old threat that was probably deployed during late 2009 and mid-2010," read a blog posting on Kaspersky's SecureList blog. "Unlike Duqu or Flame, there is no apparent cyberespionage function. ... There are very few reports of this malware at the moment, which means it's probably almost extinct."
- 8 Security Basics the Experts Want You to Know
- 10 Reasons to Fear a 'Cyber Pearl Harbor'
- 10 Best Computer Protection Software Products
Copyright 2012 TechNewsDaily, a TechMediaNetwork company. All rights reserved. This material may not be published, broadcast, rewritten or redistributed.